I hear this kind of statement all the time: ‘We use Roles/Groups for access control in our systems and applications so we’re RBAC’.
My response is an emphatic: ‘No – using roles for access control is not Role-Based Access Control!’
The first is an anti-pattern, the second a best practice. Let me explain.
RBAC is not a generic term. It refers to a specification, ANSI INCITS 359, with explicit instructions to implement. There are many posts that offer detailed explanation – including:
https://directory.apache.org/fortress/user-guide/1-intro-rbac.html
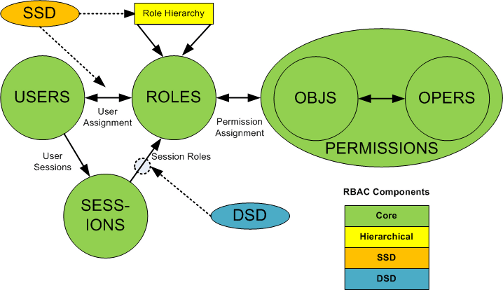
To be considered RBAC compliant an access management system, at a minimum, supports the following entities: Users, Roles, Permissions (mapping between objects and operations) and, most important – Sessions.
Sessions are the context for which role activation occurs. Just because a role has been assigned, does not mean it should be included into a particular access control decision.
This is in keeping with the principle of least privilege: Only give the user the power needed to complete their job at any particular point in time – and no more.
Doing this satisfies a multitude of requirements and we’ll talk about some in future posts.
So unless your access control system supports the session contextual object – stop calling it RBAC.
But there’s much more to it than that. RBAC specification defines the interfaces necessary for CRUD and interrogation operations. One of the most important:
This returns all permissions authorized for a user via their role assignments. And another:
authorizedPermissionUsers(Permission)
Crucial during audits – which users have access to a particular system resource? If you cannot answer this question your system lacks integrity. Many access management systems cannot accomplish these basic operations.
RBAC also defines the interface used during runtime policy enforcement operations. For example:
This returns all permissions authorized for a user via their role activations. Used by apps to cache entitlements during runtime. Without the Session entity it cannot be done. If yours cannot do this – stop calling it RBAC.
Finally there is this:
Placing roles within the access control decision paints you into a corner. This operation usually looks something like:
isUserInRole(RoleName) <— this is ok for coarse-grain but not fine-grained authZ
What if the roles change? Every change requires (some variation of) a recompile and redeployment of the application. Worse, you will need to create too many of them which pollutes your system and complicates the administration processes.
There is a better way – use a permission semantic:
checkAccess(Session, Permission)
This allows the policy enforcement point to be decoupled from the policy decision point. If the roles needed to access that resource change, the application doesn’t.
If your access management system does not do these things – stop calling it RBAC!
More to come….